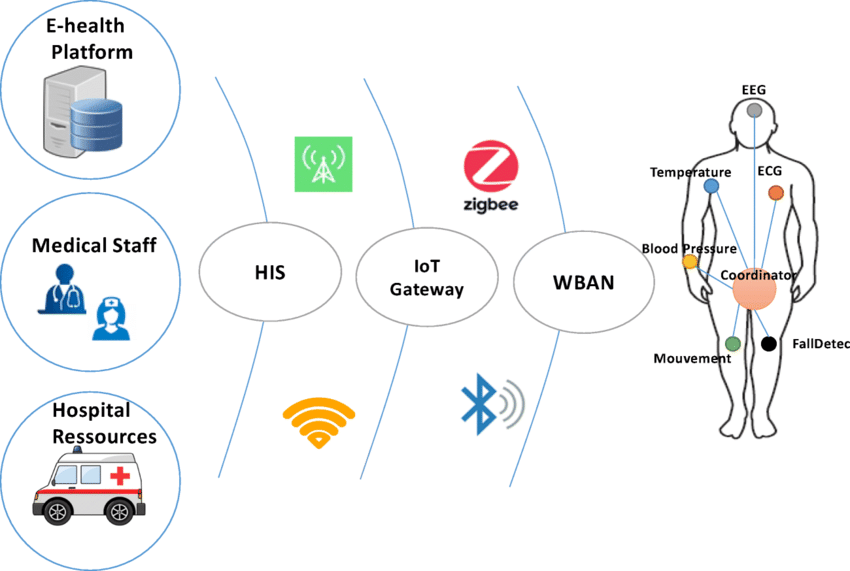
The integration of Internet of Things (IoT) technology in the healthcare sector brings forth numerous benefits, from remote patient monitoring to improved treatment outcomes. However, amidst the potential lies a critical concern: privacy and security. In this article, we delve into the intricate challenges surrounding privacy and security in IoT healthcare and explore strategies to address them effectively.
For any queries, feel free to reach us @ https://www.towardshealthcare.com/personalized-scope/5094
Understanding the Challenges
Vulnerability to Unauthorized Access
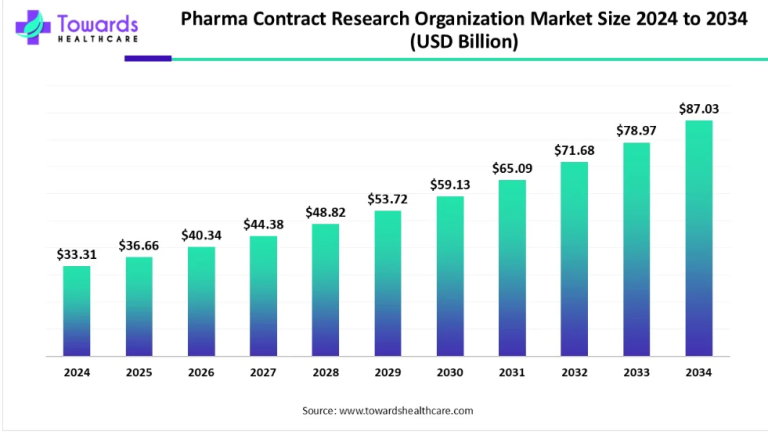
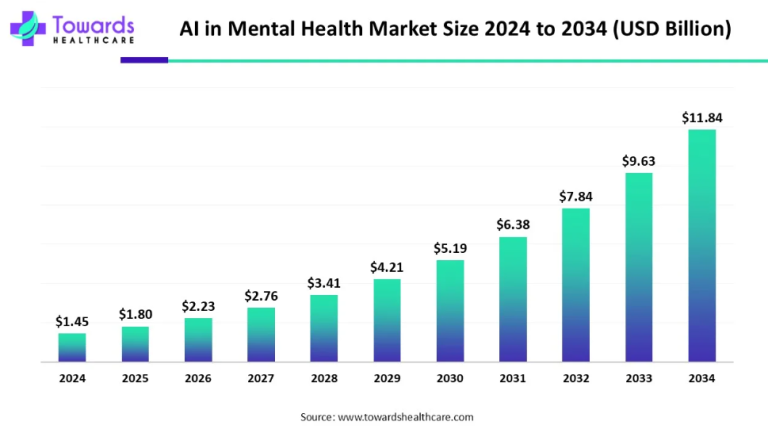
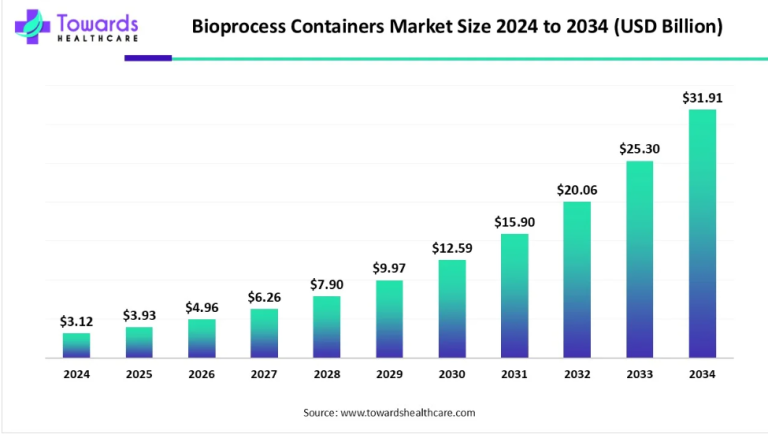
IoT devices in healthcare gather and transmit vast amounts of sensitive patient data, including medical histories, vital signs, and treatment plans. This wealth of information becomes a prime target for cyber threats, ranging from data breaches to identity theft. Without adequate safeguards, these devices are susceptible to unauthorized access, putting patient privacy at risk.
Fear of Data Breaches
The fear of data breaches looms large in the minds of both patients and healthcare providers. The ramifications of a breach extend beyond compromised privacy; they can result in financial losses, reputational damage, and legal repercussions. Such concerns act as significant barriers to the widespread adoption of IoT solutions in healthcare settings.
Strategies for Mitigation
Implementing Encryption Protocols
Encryption plays a pivotal role in safeguarding sensitive data transmitted by IoT devices. By converting information into a coded format, encryption ensures that only authorized parties can decipher it, mitigating the risk of interception by malicious actors. Robust encryption protocols, coupled with secure key management practices, form the foundation of a secure IoT ecosystem.
Enhancing Data Transmission Security
Securing the transmission of data between IoT devices and backend systems is essential for preventing unauthorized access and tampering. Secure communication protocols, such as Transport Layer Security (TLS), encrypt data during transit, thwarting interception attempts. Additionally, employing techniques like message authentication and integrity checking adds an extra layer of protection against data manipulation.
Enforcing Access Controls
Granular access controls limit the exposure of sensitive data to authorized personnel, reducing the likelihood of unauthorized access. Role-based access control (RBAC) mechanisms assign permissions based on users’ roles and responsibilities, ensuring that each individual can only access information pertinent to their tasks. Regular audits and access reviews help identify and rectify any anomalies or unauthorized access attempts promptly.
Regulatory Compliance
Adhering to HIPAA Standards
The Health Insurance Portability and Accountability Act (HIPAA) sets forth stringent guidelines for protecting patient health information in the United States. Compliance with HIPAA regulations is non-negotiable for entities handling healthcare data, including IoT device manufacturers and healthcare providers. Adhering to HIPAA standards not only mitigates legal risks but also fosters trust among patients and stakeholders.
Building Trust and Confidence
Transparency and Accountability
Transparency regarding data handling practices instills confidence among patients and stakeholders. Clear communication about how data is collected, stored, and utilized helps alleviate concerns regarding privacy and security. Furthermore, establishing accountability mechanisms, such as incident response plans and breach notification procedures, demonstrates a commitment to addressing security incidents promptly and transparently.
Continuous Monitoring and Improvement
Security is not a one-time effort but a continuous process of monitoring and improvement. Regular security assessments, penetration testing, and vulnerability scans help identify and remediate potential weaknesses in IoT infrastructure proactively. By staying abreast of emerging threats and evolving security best practices, healthcare organizations can adapt their security posture to mitigate new risks effectively.
Privacy and security constraints pose significant challenges to the widespread adoption of IoT in healthcare. However, by implementing robust security measures, adhering to regulatory standards, and fostering transparency and accountability, these challenges can be overcome. By prioritizing privacy and security, the healthcare industry can harness the full potential of IoT technologies to revolutionize patient care while safeguarding sensitive health information.
The expansion of IoT in healthcare hinges on the ability to address privacy and security concerns effectively. By embracing encryption, enhancing data transmission security, enforcing access controls, and complying with regulatory standards like HIPAA, stakeholders can build trust and confidence in IoT solutions. Through continuous monitoring and improvement, the healthcare sector can navigate the complexities of privacy and security, unlocking the transformative power of IoT to enhance patient outcomes and revolutionize healthcare delivery.
To Own Our Premium Study Instantly, Click here @ https://www.towardshealthcare.com/price/5094
Access our Premium Real Time Data Intelligence Tool, Visit: www.precedencestatistics.com
Read More Related Snapshots to IoT in Healthcare Industry